ost Preview
Key Takeaways:
- Unified Threat Management (UTM) simplifies cybersecurity by integrating multiple security functionalities into a single solution.
- UTM systems can significantly reduce costs and complexity in managing enterprise security.
- Critical features of UTM include firewall protection, antivirus, content filtering, and intrusion prevention.
- Implementing UTM can help organizations comply with regulatory requirements and enhance network security.
Introduction to Unified Threat Management
In today’s digital age, network security is becoming increasingly complex. Unified Threat Management (UTM) solutions are designed to address this complexity by integrating various security functions into one powerful system, making it easier for enterprises to manage their cybersecurity needs. UTM provides a streamlined and effective defense against many cyber threats by consolidating numerous security measures. This integration improves the overall efficiency of security operations and ensures that every aspect of the network is protected seamlessly, reducing vulnerabilities and potential breaches.
Given the escalating nature of cyber threats, businesses need a robust defense mechanism that can adapt and respond proactively. UTM is an all-encompassing shield that fortifies the network’s defenses against evolving threats such as malware, ransomware, phishing attacks, and more. Companies adopting UTM solutions benefit from a coherent strategy that enhances their cybersecurity posture, ensuring that internal and external threats are mitigated effectively. This approach simplifies the security infrastructure and offers a scalable solution that can grow with the organization, making it a cost-effective choice in the long run.
What is Unified Threat Management?
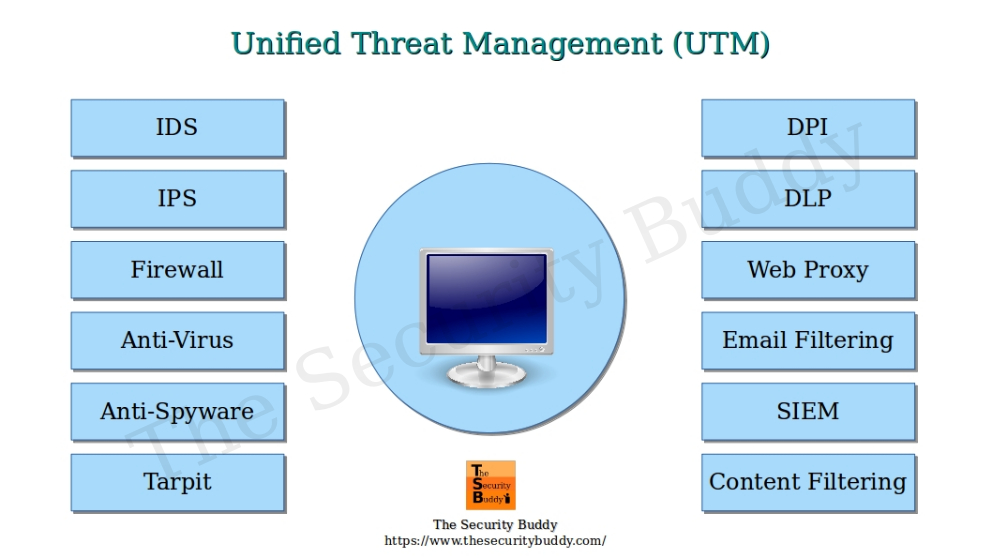
Unified Threat Management, often called UTM, is an approach to cybersecurity that consolidates multiple security measures into a single, cohesive system. This methodology streamlines security management, offering businesses a more convenient and effective way to protect their information systems. According to a recent study, adopting UTM can elevate your overall cyber defense. UTM provides a more comprehensive and synchronized defense strategy by combining different security functionalities such as firewalls, intrusion detection systems, antivirus programs, and content filtering tools into one unified platform.
This unified approach helps ensure that different security protocols work together seamlessly, reducing the likelihood of gaps in the network that cybercriminals could exploit. For businesses, this means having a more resilient and robust defense framework that simultaneously addresses multiple aspects of network security. Additionally, UTM solutions often come with user-friendly interfaces that make it easier for IT administrators to monitor and manage security protocols, ensuring that the network remains secure without unnecessarily complicating the management process.
Key Features of UTM
- Firewall Protection: Acts as the first line of defense against unauthorized access, ensuring that no unwanted traffic gets in or out of the network.
- Antivirus and Anti-Malware: These features scan and remove malicious software before it infiltrates your network. They are crucial in defending against viruses, trojans, and other types of malware that can compromise system integrity.
- Content Filtering: Blocks access to inappropriate or harmful web content, ensuring users are safe from phishing sites, adult content, and other harmful websites. This feature is particularly beneficial for organizations that comply with internet usage regulations.
- Intrusion Prevention: Detects and blocks potentially malicious actions and network breaches before they can harm the system. This proactive approach helps identify and neutralize threats before they cause significant damage.
- Virtual Private Network (VPN): This feature provides secure remote access to the company’s network, allowing employees to connect safely from various locations. It is essential in the current remote working environment to ensure remote employees maintain a secure connection to the company’s resources.
Benefits of Implementing UTM in Your Organization
Integrating a Unified Threat Management system into your network infrastructure can offer numerous benefits. It centralizes your security measures, enhances efficiency, reduces costs, and increases flexibility. Many businesses have seen a marked improvement in their security posture after adopting UTM solutions. Organizations can simplify their management processes and gain a holistic view of their security landscape by having a single control point for various security aspects.
Moreover, UTM solutions provide comprehensive reporting and alerting features that help administrators quickly identify and respond to potential threats. This real-time visibility into network activity ensures that anomalies are detected early, reducing the risk of a successful attack. Additionally, with UTM, businesses can achieve compliance with industry regulations more efficiently, as these solutions include features specifically designed to meet regulatory standards.
Challenges and Solutions in UTM Implementation
While the advantages are clear, implementing UTM has its challenges. Some common issues include high initial costs, complexity in deployment, and the need for regular updates. However, selecting a reputable provider and ensuring employee training can mitigate these challenges.
Engaging with vendors who offer comprehensive support and frequent updates is vital to keep the system robust against new threats. Additionally, businesses should consider conducting regular training sessions for their IT staff to ensure they are well-versed in the latest security protocols and UTM functionalities. This ongoing education helps maintain an effective security posture and allows the organization to adapt quickly to emerging threats or vulnerabilities.
How to Choose the Right UTM Solution
Selecting the appropriate UTM solution for your organization involves considering scalability, ease of use, cost, and vendor reputation. Conduct thorough research and engage with multiple providers to find a solution that aligns with your needs and goals. It’s essential to choose a UTM solution that meets your current requirements and can scale with your business as you grow, ensuring long-term security and peace of mind.
Businesses should also consider the level of customer support and training the vendor provides. A reliable support system ensures that any issues are addressed promptly, minimizing potential disruptions to your network security. Additionally, it is beneficial to choose a UTM solution that offers customizable features, allowing you to tailor the security measures to suit your organization’s unique requirements. Considering these factors, you can select a UTM solution that provides comprehensive protection while being cost-effective and easy to manage.
Conclusion
Unified Threat Management represents a holistic approach to cybersecurity, offering a comprehensive suite of tools that can be managed from a single platform. By centralizing your security measures, UTM can simplify your cybersecurity operations, reduce costs, and enhance the robustness of your defenses against evolving threats. Investing in UTM is a forward-thinking strategy that can provide significant returns regarding network security and peace of mind.
In conclusion, the need for a comprehensive and integrated security solution becomes paramount as cyber threats become more sophisticated. UTM offers a viable and practical approach to safeguarding your organization’s digital assets, ensuring that all aspects of network security are addressed in a unified manner. By adopting UTM, businesses can avoid potential threats, providing a secure and resilient network environment.